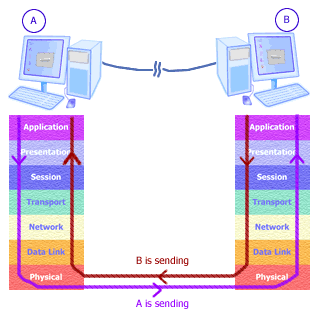
Lets Start OSI
OSI-Open Systems Interconnect. It was developed in 1984 by (ISO).
By this we can know the mechanism of sending data fro one PC to anyother.
It Includes 7 layers
While Receiving data And While Sending data
7.. Application 1.Application
6.. Presentation 2.Presentation
5.. Session 3.Session
4.. Transport 4.Transport
3.. Network 5.Network
2.. Data Link 6.Data Link
1.. Physical 7.Physical
Each And Every layer has Its own Role. I'll tell u all in details.
The O.S.I. model (O.S.I. - Open System Interconnection) is a way of sub-dividing a System into smaller parts (called layers) from the point of view of communications.
A layer is a collection of conceptually similar functions that provide services to the layer above it and receives services from the layer below it. On each layer an instance provides services to the instances at the layer above and requests service from the layer below. For example,
a layer that provides error-free communications, across a network provides the path needed by applications above it, while it calls the next lower layer to send and receive packets that make up the contents of the path. Conceptually two instances at one layer are connected by a horizontal protocol connection on that layer.
Virtually all networks in use today are based in some fashion on the Open Systems Interconnection (OSI) standard.
The core of this standard is the OSI Reference Model, a set of seven layers that define the different stages that data must go through to travel from one device to another over a network. In this article, you'll find out all about the OSI standard.
Layer 7: Application - This is the layer that actually interacts with the operating system or application whenever the user chooses to transfer files, read messages or perform other network-related activities.
Layer 6: Presentation - Layer 6 takes the data provided by the Application layer and converts it into a standard format that the other layers can understand.
Layer 5: Session - Layer 5 establishes, maintains and ends communication with the receiving device.
Layer 4: Transport - This layer maintains flow control of data and provides for error checking and recovery of data between the devices. Flow control means that the Transport layer looks to see if data is coming from more than one application and integrates each application's data into a single stream for the physical network.
Layer 3: Network - The way that the data will be sent to the recipient device is determined in this layer. Logical protocols, routing and addressing are handled here.
Layer 2: Data - In this layer, the appropriate physical protocol is assigned to the data. Also, the type of network and the packet sequencing is defined.
Layer 1: Physical - This is the level of the actual hardware. It defines the physical characteristics of the network such as connections, voltage levels and timing.
To help remember the layers names of the OSI model, try the following mnemonic device (Moving from the bottom layer to the top layer)
Layer Name Mnemonic
Layer 7......................Application.........................Away
Layer 6......................Presentation......................Pizza
Layer 5......................Sessions............................Sausage
Layer 4......................Transport...........................Throw
Layer 3......................Network.............................Not
Layer 2......................Data link.............................Do
Layer 1......................Physical..............................Please
while going 1 to 7 we can say
Please Do Not Take Sausage Pizza Away
And While Going 7th to 1st
Andhra Pradesh Se Train New Delhi Pahuchi
Lets Come To layers
1) Application layer: - This layer directly interacts with the user.
* Application layer provides a way for the network application like internet browser etc.
* The application layer provides the interface between application and network.
* It specifies many important network services that are used on the internet.
These include:-
1) HTTP
2) Telnet
3) FTP
4) TFTP
5) SNMP
2) Presentation Layer: - It presents the data into particular format like ASCII, MP3, MPEG, DOC, TEXT etc.
There are 3 works done by presentation layers.
* Encryption and decryption.
* Compression and decompression.
* Encapsulation and de-capsulation.
The presentation layer formats data for the application layer .Therefore; it also sets standards for multimedia and other file formats.
These include standard file format such as:
1) IPEG, BMP, TIFF, PICT.
2) MPEG,WMV,AVI,
3) ASCII, EBCDIC.
4) MIDI,WAV
3) Sessions Layer: -Creates maintains and terminates the session between sender and receiver.
* The Session layer protocols and interfaces co-ordinates requests and responses between different hosts using the same application.
These Protocols and interface include:
1) Network file system (NFS)
2) Apple Session protocol (ASP)
4.) Transport Layer: - Transport layer provides end to end data transfer between sender and receiver .It provides a transition between upper layer and lower layers of OSI model.
*.... It has 6 works to do :-
1).... It decides whether TCP or UDP is to be used:-
TCP – Transmission control protocol.
UDP- User data-gram protocol.
Following are the differences between TCP And UDP
...................TCP................................................................... UDP
a)......It is reliable................................................Unreliable
b)......TCP supports acknowledgment............... Doesn’t support acknowledgment.
c)......Slow...........................................................Fast
d)......Supports 3 way hand shake......................Supports one way handshake.
e)......Used for data.............................................Used for voice and video.
f)......TCP is connection oriented........................ UDP is connection less.
2).... Segmentation and desegmentation :-
Segmentation means breaking the data into smaller parts and desegmentation means reassembling those parts.
Segmentation in done at sender’s side.
And desegmentation is done at receiver’s side.
3).... Sequencing and rearranging:-
Sequencing means giving sequence number to the segment .It is done at sender’s side.
Rearranging means arranging those segments. It is done at receiver’s side.
4).... Multiplexing and demultiplexing:-
Multiplexing means one sender, many receivers.
Demultiplexing means many senders, one receiver.
5).... Error control:-
It checks for the lost segment and resends it.
6).... Flow control :-
It is also known as windowing. It controls the transmission speed.
Notes:-
Protocols that work at transport layer are TCP, UDP.
Transport layer Facts:-
The transport layer receiver large packets of information from higher layer and breaks of into smaller packets called segment.
Segmentation is necessary to enable the data to meet network size and format uses packet sequence number to reassemble segments into the original message.
5.) Network Layer:-
It adds IP address information to the packets.
Facts:-
The network layer describes how data is routed across network and on to the destination.
Network layer functions include:-
• Maintaining addresses of neighboring router.
• Maintaining a list of known networks.
The network layer uses a logical address for identifying hosts and making routing decisions. The types of addresses used are determined by the protocol.
*.... IP uses IP addresses that identify both the logical network and host addresses.
*.... IP X uses an 8 digit hexadecimal number for the network called for the host addresses.
*.... Apple talk uses a network number, ranging from 1 to 65,278 and a host number, ranging from 1 to 253.
*.... Hardware devices related to the network layer include:
•____Routers
•____Layer 3 switches.
Note
Devices that operate at the network layer read the logical address to make forwarding and receiving decisions.
Contrast their with devices that operate at the data link layer which read the MAC address.
*.... Protocols that work on network layer are IP, IPX, and apple talk.
6.) Data Link Layer :-
Data link layer is divided into 2 parts.
1) LLC – Logical link control.
2) MAC – Media access control.
Data link Facts:-
The data link layer defines the rules and procedures for hosts as they access the physical layer.
These rules and procedures specify or define:-
1) How hosts on the network are identified.
2) How the network medium can be accessed.
3) How to verify that the data received from the physical layer is error free.
It is divided into 2 sub layers:-
1) MAC: - Media access control.
The media access control layer defines specifications for controlling access to the media. The MAC sub layers are responsible for:-
*....Adding cyclical redundancy check for error checking.
*....Converting frames into bits to be sent across the network.
*....Identifying network devices and network topologies in preparation for media transmission.
*....Define an address (such as MAC address) for ex: - through CSMA/CD, CSMA/CA or token passing.
2) LLC
The logical link control layer provides an interface between the MAC layer and upper protocols.
LLC protocols are defined by the IEEE 802.2 committee. The LLC sub layer is responsible for:-
*....Maintaining orderly delivery of frames through sequencing.
*....Controlling the flow of rate of transmission.
*....Ensuring error free reception of message by retransmitting.
*....Converting data into an acceptable from the upper layers.
*.... Removing framing information from the packet and forwarding the message to the network layer.
*.... Provide a way for upper layers of the OSI model to use any MAC layer protocol.
The following network devices are associated with the data link layer.
*.... Nic card with external.
Data link layer adds MAC address information to the packets and makes it frames.
Diff between IP And Mac
......................IP.........................................................MAC
a).............32 bit.......................................................48 bit
b) Logical (changeable)...........................................Physical (unchangeable)
c) Divided into 4 parts.............................................12 parts
d) Separated by dot (.)............................................Separated By (:)
*....First 24 bits of MAC addresses is provided by IEEE, and the remaining 24 bits are company specific.
7.)Physical layer:-
It converts data into bits and sends them across the media.
*.... Facts
The physical layer of the OSI model sets standards for sending and receiving electrical signals between devices .It describes how digital data (bits) are converted to electrical pulses radio waves or pulses of light.
Hardware associated with physical layer include:-
1) Transmission media (cable and wires) media connector’s repeaters and hubs.
*.... Encapsulation of data on all layers
*.... Encapsulation of data on all layers:-
A – Data – PDU – protocols data unit.
P – Data
S – Data
T – Segment
N – Segment + IP (packet)
D – Packet + MAC Frame
P – Bits
Layers Works In Short:
A – Create
P – Present
S – Create a session
T – End to end data transfer
N – Gives the path
D – Adds MAC addresses and provides CRC check.
P – Convert the data into bits.
OSI-Open Systems Interconnect. It was developed in 1984 by (ISO).
By this we can know the mechanism of sending data fro one PC to anyother.
It Includes 7 layers
While Receiving data And While Sending data
7.. Application 1.Application
6.. Presentation 2.Presentation
5.. Session 3.Session
4.. Transport 4.Transport
3.. Network 5.Network
2.. Data Link 6.Data Link
1.. Physical 7.Physical
Each And Every layer has Its own Role. I'll tell u all in details.
The O.S.I. model (O.S.I. - Open System Interconnection) is a way of sub-dividing a System into smaller parts (called layers) from the point of view of communications.
A layer is a collection of conceptually similar functions that provide services to the layer above it and receives services from the layer below it. On each layer an instance provides services to the instances at the layer above and requests service from the layer below. For example,
a layer that provides error-free communications, across a network provides the path needed by applications above it, while it calls the next lower layer to send and receive packets that make up the contents of the path. Conceptually two instances at one layer are connected by a horizontal protocol connection on that layer.
Virtually all networks in use today are based in some fashion on the Open Systems Interconnection (OSI) standard.
The core of this standard is the OSI Reference Model, a set of seven layers that define the different stages that data must go through to travel from one device to another over a network. In this article, you'll find out all about the OSI standard.
Layer 7: Application - This is the layer that actually interacts with the operating system or application whenever the user chooses to transfer files, read messages or perform other network-related activities.
Layer 6: Presentation - Layer 6 takes the data provided by the Application layer and converts it into a standard format that the other layers can understand.
Layer 5: Session - Layer 5 establishes, maintains and ends communication with the receiving device.
Layer 4: Transport - This layer maintains flow control of data and provides for error checking and recovery of data between the devices. Flow control means that the Transport layer looks to see if data is coming from more than one application and integrates each application's data into a single stream for the physical network.
Layer 3: Network - The way that the data will be sent to the recipient device is determined in this layer. Logical protocols, routing and addressing are handled here.
Layer 2: Data - In this layer, the appropriate physical protocol is assigned to the data. Also, the type of network and the packet sequencing is defined.
Layer 1: Physical - This is the level of the actual hardware. It defines the physical characteristics of the network such as connections, voltage levels and timing.
To help remember the layers names of the OSI model, try the following mnemonic device (Moving from the bottom layer to the top layer)
Layer Name Mnemonic
Layer 7......................Application.........................Away
Layer 6......................Presentation......................Pizza
Layer 5......................Sessions............................Sausage
Layer 4......................Transport...........................Throw
Layer 3......................Network.............................Not
Layer 2......................Data link.............................Do
Layer 1......................Physical..............................Please
while going 1 to 7 we can say
Please Do Not Take Sausage Pizza Away
And While Going 7th to 1st
Andhra Pradesh Se Train New Delhi Pahuchi
Lets Come To layers
1) Application layer: - This layer directly interacts with the user.
* Application layer provides a way for the network application like internet browser etc.
* The application layer provides the interface between application and network.
* It specifies many important network services that are used on the internet.
These include:-
1) HTTP
2) Telnet
3) FTP
4) TFTP
5) SNMP
2) Presentation Layer: - It presents the data into particular format like ASCII, MP3, MPEG, DOC, TEXT etc.
There are 3 works done by presentation layers.
* Encryption and decryption.
* Compression and decompression.
* Encapsulation and de-capsulation.
The presentation layer formats data for the application layer .Therefore; it also sets standards for multimedia and other file formats.
These include standard file format such as:
1) IPEG, BMP, TIFF, PICT.
2) MPEG,WMV,AVI,
3) ASCII, EBCDIC.
4) MIDI,WAV
3) Sessions Layer: -Creates maintains and terminates the session between sender and receiver.
* The Session layer protocols and interfaces co-ordinates requests and responses between different hosts using the same application.
These Protocols and interface include:
1) Network file system (NFS)
2) Apple Session protocol (ASP)
4.) Transport Layer: - Transport layer provides end to end data transfer between sender and receiver .It provides a transition between upper layer and lower layers of OSI model.
*.... It has 6 works to do :-
1).... It decides whether TCP or UDP is to be used:-
TCP – Transmission control protocol.
UDP- User data-gram protocol.
Following are the differences between TCP And UDP
...................TCP................................................................... UDP
a)......It is reliable................................................Unreliable
b)......TCP supports acknowledgment............... Doesn’t support acknowledgment.
c)......Slow...........................................................Fast
d)......Supports 3 way hand shake......................Supports one way handshake.
e)......Used for data.............................................Used for voice and video.
f)......TCP is connection oriented........................ UDP is connection less.
2).... Segmentation and desegmentation :-
Segmentation means breaking the data into smaller parts and desegmentation means reassembling those parts.
Segmentation in done at sender’s side.
And desegmentation is done at receiver’s side.
3).... Sequencing and rearranging:-
Sequencing means giving sequence number to the segment .It is done at sender’s side.
Rearranging means arranging those segments. It is done at receiver’s side.
4).... Multiplexing and demultiplexing:-
Multiplexing means one sender, many receivers.
Demultiplexing means many senders, one receiver.
5).... Error control:-
It checks for the lost segment and resends it.
6).... Flow control :-
It is also known as windowing. It controls the transmission speed.
Notes:-
Protocols that work at transport layer are TCP, UDP.
Transport layer Facts:-
The transport layer receiver large packets of information from higher layer and breaks of into smaller packets called segment.
Segmentation is necessary to enable the data to meet network size and format uses packet sequence number to reassemble segments into the original message.
5.) Network Layer:-
It adds IP address information to the packets.
Facts:-
The network layer describes how data is routed across network and on to the destination.
Network layer functions include:-
• Maintaining addresses of neighboring router.
• Maintaining a list of known networks.
The network layer uses a logical address for identifying hosts and making routing decisions. The types of addresses used are determined by the protocol.
*.... IP uses IP addresses that identify both the logical network and host addresses.
*.... IP X uses an 8 digit hexadecimal number for the network called for the host addresses.
*.... Apple talk uses a network number, ranging from 1 to 65,278 and a host number, ranging from 1 to 253.
*.... Hardware devices related to the network layer include:
•____Routers
•____Layer 3 switches.
Note
Devices that operate at the network layer read the logical address to make forwarding and receiving decisions.
Contrast their with devices that operate at the data link layer which read the MAC address.
*.... Protocols that work on network layer are IP, IPX, and apple talk.
6.) Data Link Layer :-
Data link layer is divided into 2 parts.
1) LLC – Logical link control.
2) MAC – Media access control.
Data link Facts:-
The data link layer defines the rules and procedures for hosts as they access the physical layer.
These rules and procedures specify or define:-
1) How hosts on the network are identified.
2) How the network medium can be accessed.
3) How to verify that the data received from the physical layer is error free.
It is divided into 2 sub layers:-
1) MAC: - Media access control.
The media access control layer defines specifications for controlling access to the media. The MAC sub layers are responsible for:-
*....Adding cyclical redundancy check for error checking.
*....Converting frames into bits to be sent across the network.
*....Identifying network devices and network topologies in preparation for media transmission.
*....Define an address (such as MAC address) for ex: - through CSMA/CD, CSMA/CA or token passing.
2) LLC
The logical link control layer provides an interface between the MAC layer and upper protocols.
LLC protocols are defined by the IEEE 802.2 committee. The LLC sub layer is responsible for:-
*....Maintaining orderly delivery of frames through sequencing.
*....Controlling the flow of rate of transmission.
*....Ensuring error free reception of message by retransmitting.
*....Converting data into an acceptable from the upper layers.
*.... Removing framing information from the packet and forwarding the message to the network layer.
*.... Provide a way for upper layers of the OSI model to use any MAC layer protocol.
The following network devices are associated with the data link layer.
*.... Nic card with external.
Data link layer adds MAC address information to the packets and makes it frames.
Diff between IP And Mac
......................IP.........................................................MAC
a).............32 bit.......................................................48 bit
b) Logical (changeable)...........................................Physical (unchangeable)
c) Divided into 4 parts.............................................12 parts
d) Separated by dot (.)............................................Separated By (:)
*....First 24 bits of MAC addresses is provided by IEEE, and the remaining 24 bits are company specific.
7.)Physical layer:-
It converts data into bits and sends them across the media.
*.... Facts
The physical layer of the OSI model sets standards for sending and receiving electrical signals between devices .It describes how digital data (bits) are converted to electrical pulses radio waves or pulses of light.
Hardware associated with physical layer include:-
1) Transmission media (cable and wires) media connector’s repeaters and hubs.
*.... Encapsulation of data on all layers
*.... Encapsulation of data on all layers:-
A – Data – PDU – protocols data unit.
P – Data
S – Data
T – Segment
N – Segment + IP (packet)
D – Packet + MAC Frame
P – Bits
Layers Works In Short:
A – Create
P – Present
S – Create a session
T – End to end data transfer
N – Gives the path
D – Adds MAC addresses and provides CRC check.
P – Convert the data into bits.